With a shortage of accountants in the US, CPA firms are looking to outsource their services to offshore locations like India. While it is a reasonable decision from a cost and capacity perspective, it is crucial to be aware of the potential risks associated with sharing client’s confidential data. According to a 2025 Deloitte report on cybersecurity in accounting, there has been a 300% surge in attacks targeting the industry. The report goes on to survey 34.5% of firms that reported at least one cybersecurity attack over the last year – (2024-2025).
These numbers should be a cause for concern in the accounting world. The misses clearly indicate a lack of due diligence from firms looking to outsource. Indications from AICPA’s vendor due diligence checklist show that firms are focusing on parameters such as cost, speed of service, and technical expertise. While these are all very pertinent to a firm’s success, they often miss out on the crucial element of cybersecurity.
From a regulatory standpoint, while there are a number of security frameworks, such as SOC 2 and ISO 27001, it’s easy to get blindsided by what the compliance mandates actually entail. In addition to compliance readiness, firms that are looking to outsource should be aware of certain best practices when it comes to cybersecurity for accounting.
Cybersecurity in Accounting–Best Practices to Keep Your Client’s Data Secure
At AcoBloom, data security is of the highest importance. We value visibility and transparency with our clients to build an environment of trust and loyalty. Over the years, we are proud to state that our record on data security has largely remained unblemished. This is primarily down to the data security policy established by the organization and strict adherence to said policies by the internal teams.
While this is not a comprehensive list of all best practices in data security, the list below gives a sense of the direction and seriousness of keeping client confidential data secure.
Data Collection Through Secure Channels
Accounting firms share their clients’ confidential data only through secure channels. This data is then handled by a dedicated Client Advisor, who provides limited access to respective teams to work on through secure internal networks. At no time can this data be downloaded or shared internally by any other means other than the one prescribed in the data security policy. Once the work gets submitted, it is automatically deleted from all internal shared drives.
Clients can share their data through any of the below secure channels:
- Remote Desktop Protocol (RDP)
RDP is possibly the most secure channel for sharing confidential information between two or more users. It is a set of protocols that allow users to interact with different systems under the same server, through various devices, remotely. The admin specifies who gains access to certain files, applications, and can perform specific tasks within the virtual machine. Before connecting to an RDP a secure VPN must be established to encrypt traffic and secure IP.
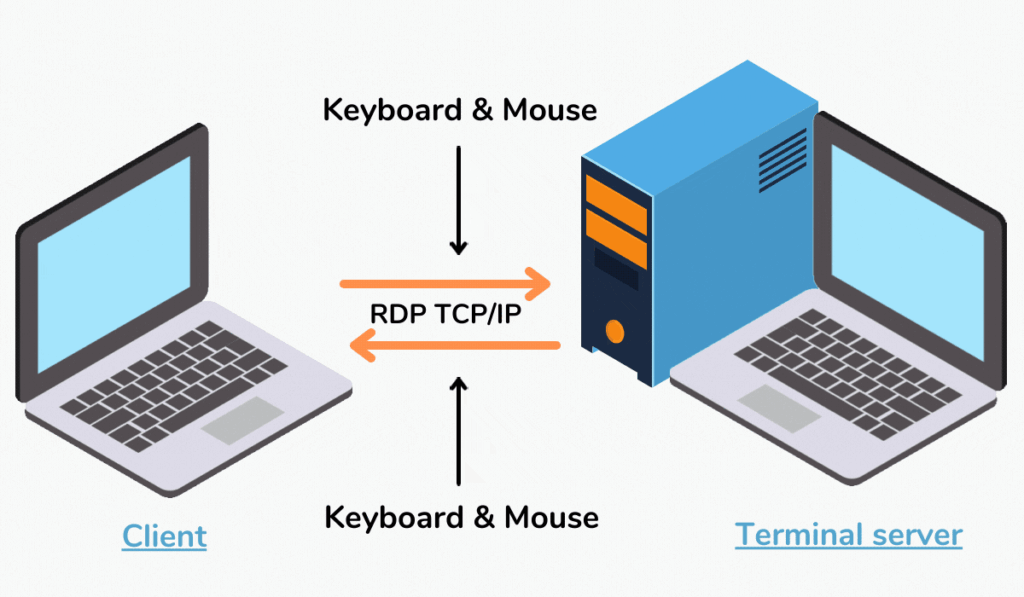
Another feature of RDP is the implementing of Multi Factor Authentication (MFA), which acts as an additional layer of security. MFA requiring users to provide more than one form of verification to access a system or account usually done through a mobile device. It involves combining a password with an additional factor, such as a code, a biometric scan, or a push notification. MFA is only carried on official mobile devices provided by the company. Users cannot conduct an MFA on their personal devices.
For added security, RDP login password automatically expires after 30 days. Throughout this process, the client maintains full access and control over the account, tax, and audit software, ensuring transparency and data integrity at every stage.
- Client’s Secure Domain
A simpler and equally secure alternative to RDP is to use a client specific domain. This is where the client adds user/s to their domain, which includes email rights and associated shared drive access. A good example is a specific domain name where the client can create a new user and provide access rights based on scope of activity or need for information. This gives the domain administrator complete control over access rights and approvals based on their preferences or policies.
- Secure Document Management Software
Another way to securely share client confidential data is through a cloud-based document management software. The client chooses a document software solution of their choice and shares their login credentials. Like the other secure data sharing options, the client can limit access to specific individuals and specific functions that the client approves should be accessible to the user. In this way, data remains secure, and access is granted for only those people responsible for that specific task.
Verito Data Security
While many of our clients know exactly what they want, there are some that are unsure about which path is right for them. For those clients, we offer a complimentary consultation about the available options and the one that is the best fit for their firm’s requirements. To ensure a seamless transition, we have partnered with Verito, a trusted cloud hosting provider for tax and accounting firms. This partnership was established to ensure that all client data is securely stored on dedicated servers with full data isolation and in compliance with SOC-2 guidelines.
Benefits to the client:
- Remote management and optimization of IT systems
- 24/7 access to certified support professionals
- Continuous monitoring, updates, and threat detection
- Tools that integrate accounting, CRM, and payments
- Regular reports on system health and backups
- Expert guidance for technology decisions
Continuous Web Traffic Monitoring
Round-the-clock monitoring of all incoming and outgoing network traffic to detect anomalies, malicious activity, or unauthorized access attempts. Detecting these suspicions in real-time is a core part of our cybersecurity strategy for accounting firms.
Any unusual activity triggers a rapid investigation, and disciplinary actions are taken where internal violations are detected. This ensures that our systems remain resilient against intrusion and data exfiltration attempts.
- Keeps data safe from unauthorized access.
- Ensures early detection of threats.
- Minimizes disruptions to your service.
Automated Security Updates and Patch Management
Cyber threats evolve quickly, and delays in updating software can leave systems vulnerable. That’s why we’ve implemented an automated patch management system that regularly checks for and applies the latest security patches, system updates, and antivirus definitions across all devices.
Our proactive approach ensures that every part of our infrastructure stays hardened against the latest known vulnerabilities, implementing best practices for cybersecurity in businesses.
- Protects data from the latest cyber threats.
- Reduces downtime due to vulnerabilities.
- Demonstrates proactive risk control.
Secured Email Infrastructure and Usage Policies
Email is one of the most sought-after channels by attackers. Since it’s so easy to send phishing and malware attacks through emails, we have enforced strict security measures on all company email platforms. These include email encryption, spam filtering, anti-phishing technology, and multifactor authentication (MFA).
All employees are trained on proper email hygiene and must adhere to our internal Email Usage Policy, which outlines cybersecurity best practices for businesses, as part of our official employee handbook, to reduce the risk of human error.
- Safeguards against phishing and email fraud.
- Ensures secure, professional communication.
- Promotes trust in every interaction.
Advanced Event Log Collection and Analysis
Event logging is an essential component for identifying early signs of a cyber incident. We maintain centralized logging systems that collect and securely store logs from across our IT environment, including endpoints, servers, firewalls, and applications.
Some of our cybersecurity best practices include having all our logs regularly reviewed using automated tools and manual analysis to uncover suspicious activity or attempted breaches. Timely log analysis has enabled us to detect and neutralize threats before they can escalate into real problems.
- Detects threats before they escalate.
- Increases system reliability.
- Speeds up response to security issues.
Robust Mobile Device Management (MDM)
Our Mobile Device Management policy ensures that only authorized, policy-compliant devices can access company data.
Every official device is secured with full-disk encryption, remote wipe capabilities, application restrictions, and mandatory device authentication. No device is exempt when it comes to maintaining cybersecurity for accounting and allowing us to maintain complete control over how and where sensitive data is accessed, even outside the office.
- Secures data on mobile devices.
- Prevents data leaks from lost or stolen hardware.
- Enables safe remote access.
Procurement from Secure-by-Design Vendors
All our systems, hardware, and software are obtained from trusted vendors who follow secure-by-design principles, meaning security is built into the product development process from the start. These vendors have shown their dedication to using secure coding practices and providing ongoing security updates to maintain cybersecurity best practices, thereby reducing third-party risks from the beginning.
- Minimizes third-party security risks.
- Guarantees use of trusted, secure systems.
- Strengthens overall system integrity.
Strict Session Management and Access Controls
To prevent unauthorized access or data misuse, we enforce comprehensive session security protocols. In that case, cybersecurity for accounting firms includes automatic session terminations after periods of inactivity, screen locking, and account lockout mechanisms after multiple failed login attempts. Access to systems and data is role-based and follows the principle of least privilege, meaning employees can only access the information necessary for their job functions.
- Prevents unauthorized access to your data.
- Reduces human error and insider threats.
- Ensures controlled and secure access.
Conclusion
Cybersecurity is now a core part of modern accounting. With rising threats and increasing data sensitivity, implementing strong cybersecurity for accounting firms is not an option; it is a must. It’s a matter of security for your business and clients to partner with a firm that prioritizes the protection of data.
At AcoBloom, we follow trusted cybersecurity best practices for businesses to keep their data safe with technology and expertise at the highest level. This ensures that your client’s data stays secure during all stages of production. If you are not sure about which direct to take, feel free to contact us for discussion on your specific data security needs.
